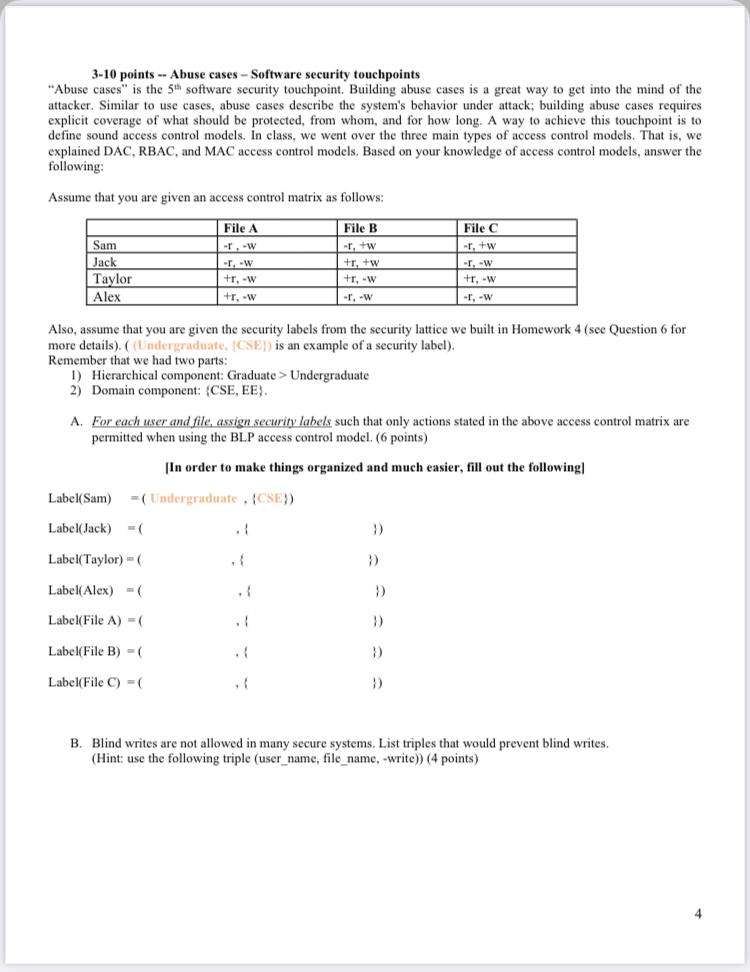
43 security labels access control
Using Security Labels for Directory Access and Replication Control - Isode The access control model is that a Security Label is associated with each entry in the directory, and that label indicates the sensitivity of the information contained in the directory entry. The example DIT "organizations", with different Security Labels. mediagazer.comMediagazer 1 day ago · Uber is investigating a breach of its computer systems, saying a hacker compromised a worker's Slack account and also gained access to other internal systems Wall Street Journal: Speaking hours after Ethereum's Merge update, SEC Chair Gary Gensler says cryptocurrencies that let holders stake coins may be subject to US securities laws Bloomberg:
› blog › network-access-control-nacWhat Is Network Access Control? Explaining NAC Solutions Jul 07, 2022 · Network access control is not a “set it and forget it” type of security control. You’ll need to make adjustments as the organization (and the threats facing it) evolve over time. Make sure you have the resources needed to continually monitor and optimize the solution before beginning an NAC implementation journey. How to choose an NAC ...
Security labels access control
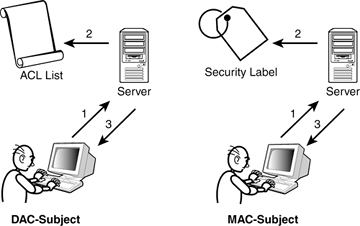
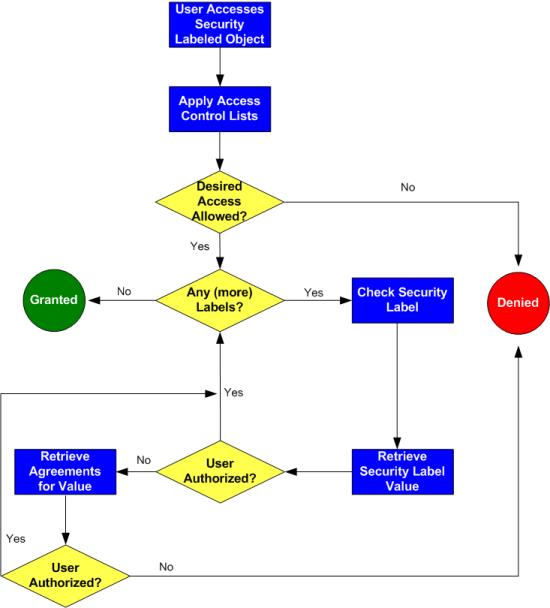
Security Labels and Access Control - support.ptc.com To access an object, a user must be cleared for all security labels, either as an authorized participant or by an active agreement, and have proper access control permissions for that object. The following flow chart provides an overview of how Windchill processes security labels and access control to grant or deny a user access to an object. Access Control using Security Labels & Security Clearance - Isode Security Labels and Security Clearance provides a mechanism for controlling access to information that works well for large numbers of users. It can be an effective approach for access control in organizations that do not use non-electronic security labels. The following diagram shows the translation of the earlier example into electronic form. docs.microsoft.com › en-us › archiveAccess Control: Understanding Windows File And Registry ... Sep 10, 2019 · Otherwise, the DACL access control entries (ACEs) are examined in order. As soon as the security system is able to show that all requested access components are allowed or that any of them is denied, it returns a success in the former case and a failure in the latter. Thus, the DACL's list of ACEs should be appropriately ordered.
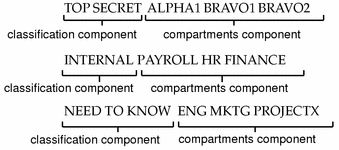
Security labels access control. How security labels control access - help.hcltechsw.com Home; Security You can secure your HCL OneDB™ database server and the data that is stored in your HCL OneDB™ databases. You can encrypt data, secure connections, control user privileges and access, and audit data security. Security in HCL OneDB™ The HCL OneDB™ Security Guide documents methods for keeping your data secure by preventing unauthorized viewing and altering of data or ... Access Control Models: MAC, DAC, RBAC, & PAM Explained MAC works by applying security labels to resources and individuals. These security labels consist of two elements: Classification and clearance — MAC relies on a classification system (restricted, secret, top-secret, etc.) that describes a resource's sensitivity. Users' security clearances determine what kinds of resources they may access. How security labels control access - ibm.com Label-based access control (LBAC) works by comparing the labels that you have associated with users against labels that you have associated with data by using a predefined rule set (IDSLBACRULES). You construct these labels with security label components, which represent different levels of data classification and access authority. Label-based access control (LBAC) overview - IBM In label-based access control (LBAC) a security label is a database object that describes a certain set of security criteria. Security labels are applied to data in order to protect the data. They are granted to users to allow them to access protected data. Format for security label values
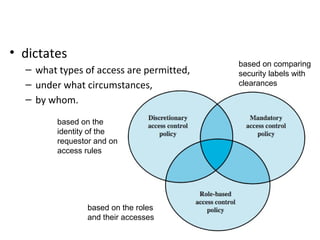
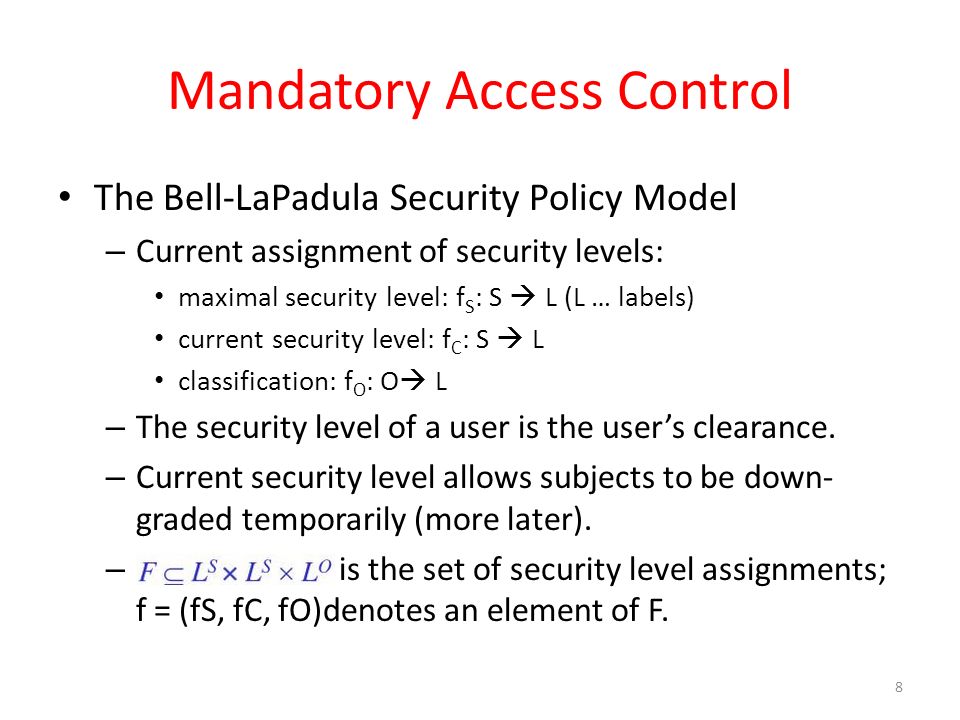
[Knowledge Hub] Windchill PLM Permissions/Access Control/Security Label Article - CS320673 [Knowledge Hub] Windchill PLM Permissions/Access Control/Security Label Modified: 24-Aug-2022 Applies To Windchill PDMLink 10.0 to 12.0 Windchill ProjectLink 10.0 to 12.0 Pro/INTRALINK 8.x + 10.0 to 12.0 Windchill PDM Essentials 10.0 to 12.0 PTC Arbortext Content Manager 10.0 to 12.0 Description How to manage access control? Mandatory access control - Wikipedia Access to the labels and control mechanisms are not [citation needed] robustly protected from corruption in protected domain maintained by a kernel. The applications a user runs are combined with the security label at which the user works in the session. Access to information, programs and devices are only weakly controlled [citation needed]. › blog › the-role-of-accessThe Role of Access Control in Information Security Nov 12, 2020 · The next type of access model is known as attribute-based access control (ABAC). According to NIST: “It represents a point on the spectrum of logical access control from simple access control lists to more capable role-based access, and finally to a highly flexible method for providing access based on the evaluation of attributes.” en.wikipedia.org › wiki › Information_securityInformation security - Wikipedia The CIA triad of confidentiality, integrity, and availability is at the heart of information security. ( The members of the classic InfoSec triad—confidentiality, integrity, and availability—are interchangeably referred to in the literature as security attributes, properties, security goals, fundamental aspects, information criteria, critical information characteristics and basic building ...
How security labels control access - help.hcltechsw.com Security labels rely on security label components to store information about the classification of data and about which users have access authority. Label-based access control (LBAC) works by comparing the labels that you have associated with users against labels that you have associated with data by using a predefined rule set (IDSLBACRULES). Access Control System Fayetteville GA | Keycards & Door Access Control ... If a keycard or fob is lost, you can simply inactivate that fob or card using your security system. Keycards or fobs can be personalized to give access to the rooms needed for each employee, so you are controlling exterior and interior entry points. Digital access control is also valuable if an employee is let go or quits. cloud.google.com › pubsub › docsAccess control with IAM | Cloud Pub/Sub Documentation ... Sep 14, 2022 · In Pub/Sub, access control can be configured at the project level and at the individual resource level. For example: Grant access on a per-topic or per-subscription basis, rather than for the whole Cloud project. If you have view-only access to a single topic or subscription, you cannot view the topic or subscription using the Google Cloud console. EOF
Security-labels - FHIR v4.3.0 - Health Level Seven International A security label is a concept attached to a resource or bundle that provides specific security metadata about the information it is fixed to. The Access Control decision engine uses the security label together with any provenance resources associated with the resource and other metadata (e.g. the resource type, resource contents, etc.) to. approve read, change, and other operations
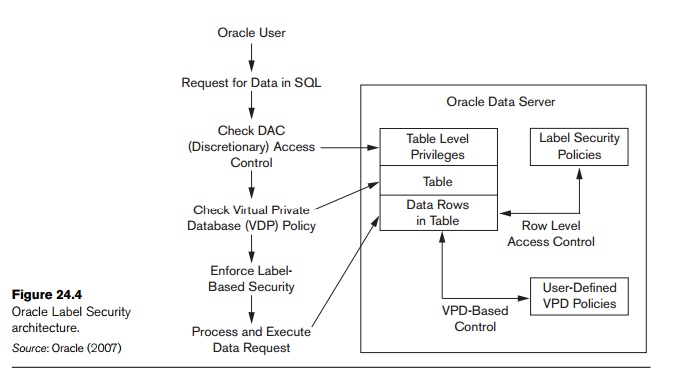
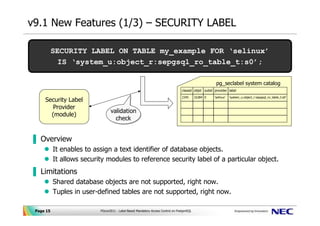
Label Security | Oracle Oracle Label Security records and enforces access permission for data based on project codes, regions, or data classifications. These controls reduce the risk of unauthorized access to sensitive data and help to demonstrate regulatory compliance. Learn more about Oracle Database security. Watch the overview video (8:16)
Access Control System Fayetteville GA | Keycards & Door Access Control ... Aaron's Home Tech understands the need for forensic-quality archive footage. Businesses need to know what happens within and around their walls and do have the footage necessary to zoom in and out while maintaining the necessary picture quality, businesses need the right security cameras. We have Full HD, 4k, and 8K security camera options ...
Home Security in Fayetteville, Fayette, Georgia - Protection 1 Protection 1 offers the best home security Fayetteville, Georgia residents rely on. Call 866.234.9412 for home security and alarm monitoring. ... a home security system also provides the option to add our remote home security access, which allows you to stay connected and in control from your web-enabled PC, Android phone or tablet, ...
Security Control Systems & Monitoring in Fayetteville, GA - Superpages We found 258 results for Home Security Systems in or near Fayetteville, GA.They also appear in other related business categories including Security Equipment & Systems Consultants, Fire Alarm Systems, and Smoke Detectors & Alarms.24 of these businesses have an A/A+ BBB rating.12 of the rated businesses have 4+ star ratings.. The businesses listed also serve surrounding cities and neighborhoods ...
› wp-content › uploadsATION TRA ANCE - White House ATION TRA ANCE 8 changing, creating new threats.China, in particular, has rapidly become more assertive. It is the only competitor potentially capable of combining its economic, diplomatic, military,
docs.microsoft.com › en-us › archiveAccess Control: Understanding Windows File And Registry ... Sep 10, 2019 · Otherwise, the DACL access control entries (ACEs) are examined in order. As soon as the security system is able to show that all requested access components are allowed or that any of them is denied, it returns a success in the former case and a failure in the latter. Thus, the DACL's list of ACEs should be appropriately ordered.
Access Control using Security Labels & Security Clearance - Isode Security Labels and Security Clearance provides a mechanism for controlling access to information that works well for large numbers of users. It can be an effective approach for access control in organizations that do not use non-electronic security labels. The following diagram shows the translation of the earlier example into electronic form.
Security Labels and Access Control - support.ptc.com To access an object, a user must be cleared for all security labels, either as an authorized participant or by an active agreement, and have proper access control permissions for that object. The following flow chart provides an overview of how Windchill processes security labels and access control to grant or deny a user access to an object.









!['Mandatory Access Control Essentials with SELinux': Costas Senekkis, ICSI [CRESTCon 2019]](https://i.ytimg.com/vi/h4eG8y53D9Q/maxresdefault.jpg)














Post a Comment for "43 security labels access control"